In the digital world, security is like the lock on your front door—something most people forget about until it fails. Among the many ways intruders can sneak in, Cross-Site Request Forgery (CSRF) remains one of the trickiest. It’s the digital equivalent of a con artist tricking someone into unlocking their house from the inside. For developers working on modern stateless applications, understanding CSRF and building strong defences against it is a critical part of responsible software craftsmanship.
Understanding CSRF Through a Real-World Analogy
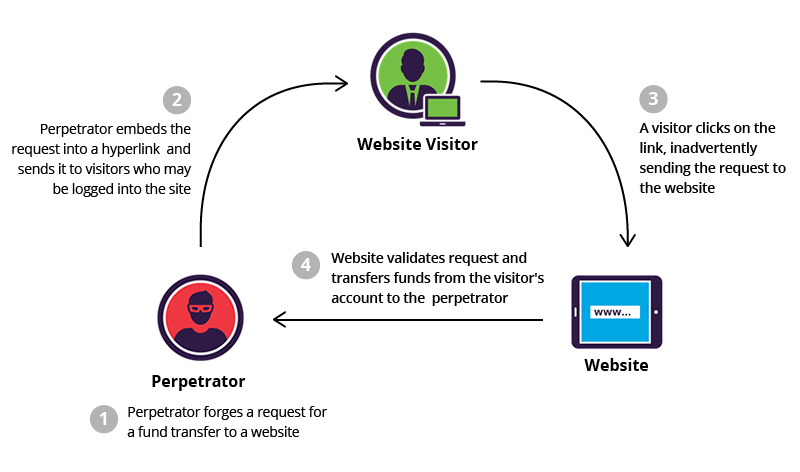
Imagine receiving an envelope that looks like it came from your bank, asking you to sign and return it. You trust it and comply—only to realise later that it wasn’t your bank at all. The attacker relied on your trust and familiarity to make you perform an action that benefits them.
CSRF works similarly. It tricks authenticated users into unknowingly executing unwanted actions, such as transferring money or changing passwords. In traditional web applications, cookies and sessions hold authentication details, making them an easy target. Modern stateless architectures have reduced the attack surface but not eliminated it entirely.
For learners building their foundation in secure coding practices, enrolling in a java full stack developer course helps understand how vulnerabilities like CSRF emerge from real-world application flow and how to neutralise them through strategic design.
Statelessness and Its Security Implications
Modern applications rely heavily on stateless design, where each request is independent and self-contained. While this design promotes scalability and simplicity, it can make implementing security a bit like locking every door in a house individually instead of using one central lock.
In stateless systems, authentication tokens replace traditional sessions. The challenge arises when these tokens—like JSON Web Tokens (JWTs)—are stored insecurely in local storage or transmitted without proper headers. Attackers can exploit weak token management to mimic user requests.
Developers must ensure that each request carries cryptographic proof of authenticity, typically through anti-forgery tokens or double-submit cookies. Such measures act as silent guards, ensuring every digital handshake is genuine.
Implementing Token-Based Defences
CSRF mitigation begins with understanding how to verify intent. Anti-forgery tokens play a vital role here. They are small, random values sent alongside legitimate requests, ensuring that actions originate from trusted sources.
In frameworks like Spring Security or Angular, developers can integrate CSRF protection seamlessly, but when building from scratch, it’s essential to ensure:
- Tokens are unique per session or per form submission.
- Tokens are tied to specific user identities.
- Validation logic rejects requests without matching tokens.
Another effective layer is the use of the SameSite cookie attribute. Setting cookies to SameSite=Strict or Lax ensures that browsers do not automatically attach cookies to cross-origin requests. This simple change can block a large percentage of CSRF attempts without altering backend logic.
Beyond Tokens: Modern Best Practices
In addition to token-based protection, developers should consider the following practices to strengthen application resilience:
- Use of Custom Headers: REST APIs can require non-standard headers (like X-Requested-With), which browsers don’t include in cross-origin requests by default.
- Content-Type Validation: Restricting accepted content types ensures that malicious form submissions are not processed.
- CORS Configuration: Cross-Origin Resource Sharing rules must be tightly configured, allowing requests only from trusted domains.
- Security Audits: Regular penetration testing and code reviews help identify weak points before attackers can exploit them.
For hands-on practitioners, structured learning through a java full stack developer course provides a practical understanding of these methods, helping developers move beyond theory to real-world implementation.
The Future of CSRF Protection
As web applications evolve toward microservices and APIs, traditional CSRF concerns are gradually giving way to newer threats such as token replay and XSS-based attacks. Yet, the principles behind CSRF mitigation—authenticating intent, verifying identity, and maintaining integrity—remain vital in any system that handles user data.
Emerging frameworks are now embedding zero-trust principles directly into their architectures, ensuring that every request, no matter how small, is verified and validated. This shift towards proactive security marks a new chapter in web development ethics and engineering responsibility.
Conclusion
CSRF is not just a technical challenge—it’s a test of how carefully we design for trust in a digital world. By understanding its mechanisms and applying layered defences, developers can ensure that every interaction in their system is intentional and secure.
As applications become more distributed and stateless, mastering these security fundamentals becomes even more crucial. Through the disciplined learning of modern frameworks and best practices, developers can confidently build systems where safety is woven into every line of code.